K8s Security: Use CIS Benchmarks for Cluster Security Assessment.
The Center for Internet Security (CIS) is a not-for-profit organization that publishes cybersecurity best practices. One of their publications is the Kubernetes CIS Benchmark (aka kube-bench), a catalog of best practices for Kubernetes environments.
Kube-bench (github repo here), as per the official description provided
is a tool that checks whether Kubernetes is deployed securely by running the checks documented in the CIS Kubernetes Benchmark.
Kubernetes engineers use kube-bench to automate the checking of Kubernetes cluster components against the CIS Benchmark by running it as a Pod on the cluster to examine.
How do I configure kube-bench as a Pod in an already active cluster?
A Pod for kube-bench is deployed the same was as every other Pod in a cluster (i.e as part of a Deployment, ReplicaSet, DaemonSet or a Job). The repo for kube-bench has YAML files for Jobs that will generate the Pod for running the checks.
At the time this article was being produced, the links to both YAML files mentioned above are:
job-master.yaml: https://github.com/aquasecurity/kube-bench/blob/main/job-master.yaml and
job-node.yaml: https://github.com/aquasecurity/kube-bench/blob/main/job-node.yaml
In case the links fail, please go to aquasecurity/kube-bench GitHub repo for updated links.
Execute the command below to configure a kube-bench Pod for checking the security exposure on the Control Plane:
$ kubectl apply -f <url to the job-master.yaml manifest>
This command will create a Job and the resulting Pod as shown in the image below:
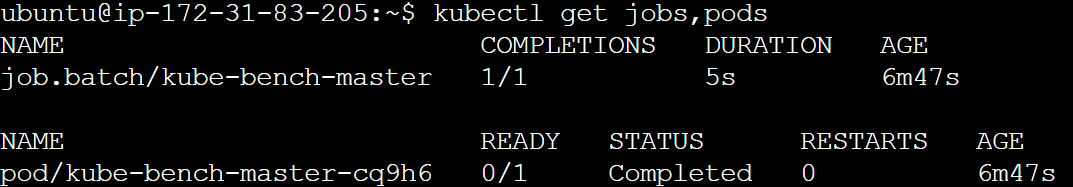
Notice the Pod shows a STATUS of Completed indicating it has already run a check on the Control Plane.
We can pipe the logs for the kube-bench-master-<hash> Pod to a text file to investigate its findings.
$ kubectl logs kube-bench-master-cq9h6 > check-output.txt
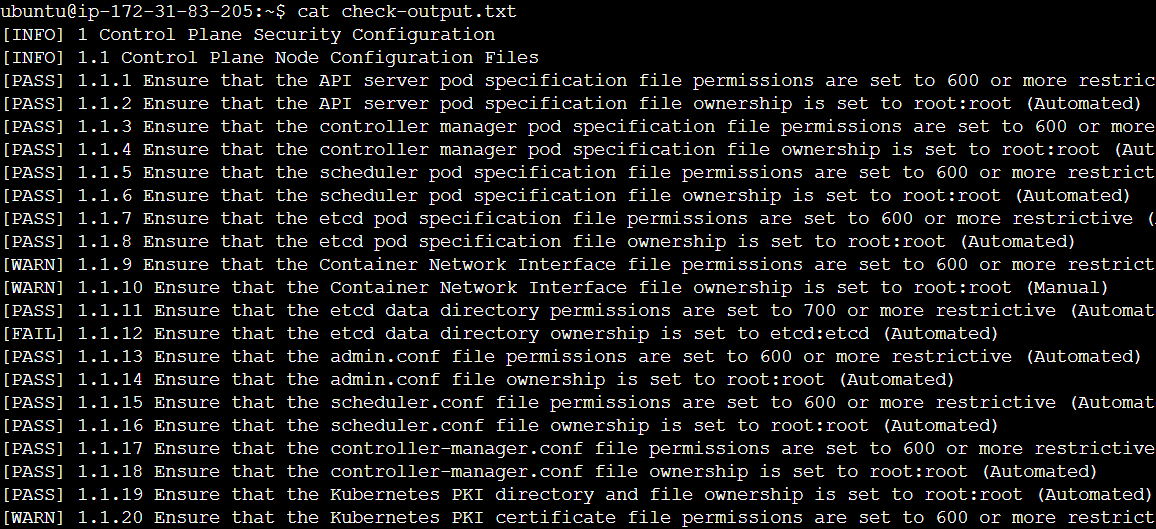
The logs are either INFO (informational), PASS (successful check against CIS) or FAIL (areas that are a potential security vulnerability).
Along with a list of INFO, PASS or FAIL logs, kube-bench will also suggest remediations for concerning security configuration gaps.
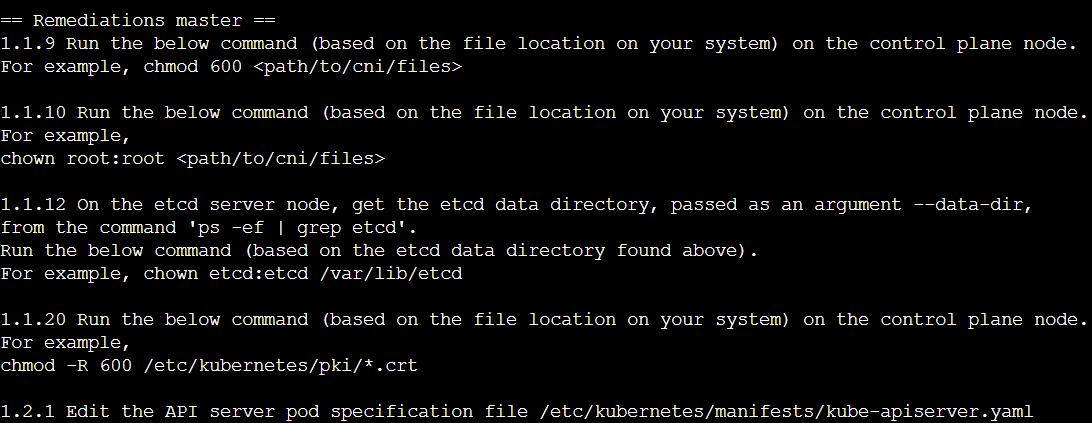
After making the suggested fixes, re-run the Job/Pod for kube-bench (delete the Job and re-apply it) and check the log outputs to confirm the vulnerability is no longer a concern.
$ kubectl delete job
$ kubectl apply -f <URL to manifest>
I write to remember and if in the process, I can help someone learn about Containers, Orchestration (Docker Compose, Kubernetes), GitOps, DevSecOps, VR/AR, Architecture, and Data Management, that is just icing on the cake.