K8s Security: Protecting Node Metadata and Endpoints when using managed Kubernetes.
All Cloud Service Provides (at least the big ones like AWS, GCP and Azure) expose a metadata service for their managed K8s service. Through these metadata services, which are really APIs, users can get access to sensitive data used for authentication. It is therefore critical that the appropriate checks and roadblocks against such unauthorized access are implemented.
A compromised Pod can become a hacker's gateway to the metadata services API.
Fortunately, there are tactics we can use to ensure such a gap in the clusters security is not left open.
Let's assume we have a managed cluster on AWS and a hacker is attempting to gain unauthorized access to our infrastructure.
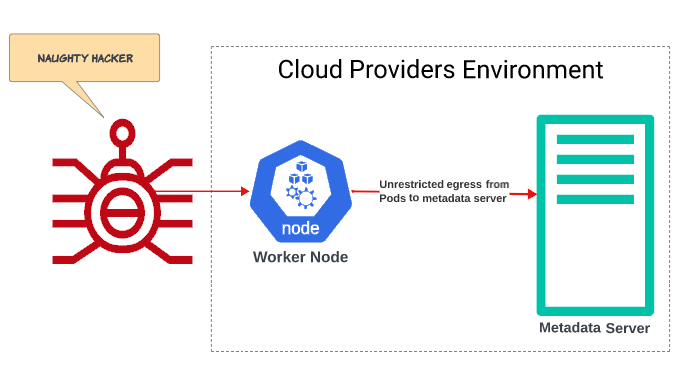
We will also assume that access to the metadata server has not been restricted in any form and the hacker will perhaps not break a sweat as he/she/they/pronoun-of-choice break through and do what malicious hackers usually do: create trouble.
How can this be avoided?
We can use constructs like NetworkPolicy to limit traffic between Worker Nodes and the metadata server.
In AWS, the metadata server can be reached with the IP address 169.254.169.254 (as noted in AWS documentation) and can provide access to EC2 instance metadata. For instance, the hacker can retrieve the local IP address of the EC2 instance acting as the Worker Node, gain access to the Pods placed on it and proceed to use this information in a number of ways. Therefore, to prevent any Pod in a namespace from reaching the IP address of the metadata server, we can construct a NetworkPolicy object, to be applied to all Pods, that allows egress traffic to all IP addresses except 169.254.169.254.
An example of a NetworkPolicy to stop all egress from a Pod to AWS metadata server is provided below:
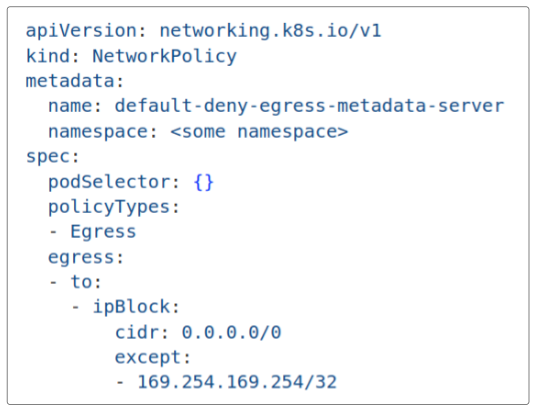
Applying this network policy to all Pods in a specific namespace will clamp down on any EGRESS traffic from those Pods to the metadata server (as indicated by the IP address shown in the except clause).

I write to remember and if in the process, I can help someone learn about Containers, Orchestration (Docker Compose, Kubernetes), GitOps, DevSecOps, VR/AR, Architecture, and Data Management, that is just icing on the cake.