K8s Security: Directional network traffic control using NetworkPolicy.
The best way to secure Pod-to-Pod network is with through the use of what is called the Principle of Least Privilege.
Least Privilege implies that a Pod should only be given just enough privilege for network communication with other Pods. In a previous article, Pod-to-Pod Networking Management using Network Policy was discussed. Here, we will take that concept and add more meat to its bones.
How can I set up a default deny-all ingress network policy?
Step 1: Write the manifest for a new NetworkPolicy.
Let's make a NetworkPolicy manifest and name it deny-all-ingress.yaml.
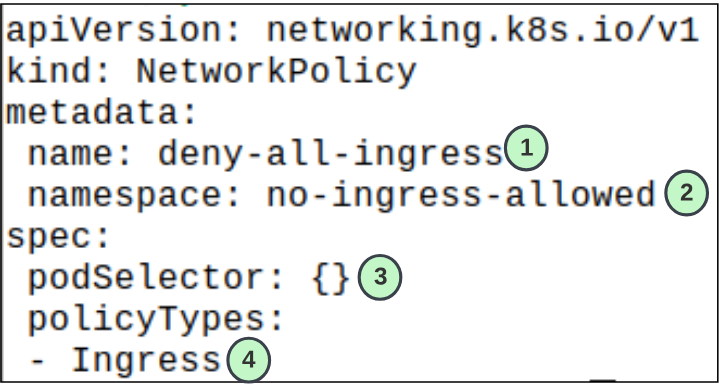
The policyTypes field indicates whether or not the given policy applies to ingress traffic to selected pod, egress traffic from selected pods, or both. If no policyTypes are specified on a NetworkPolicy then by default Ingress will always be set and Egress will be set if the NetworkPolicy has any egress rules.
ingress: Each NetworkPolicy may include a list of allowed
ingress rules. Each rule allows traffic which matches both the from and ports sections. The example policy contains a single rule, which matches traffic on a single port, from one of three sources, the first specified via an ipBlock, the second via a namespaceSelector and the third via a podSelectoregress: Each NetworkPolicy may include a list of allowed
egress rules. Each rule allows traffic which matches both the to and ports sections. The example policy contains a single rule, which matches traffic on a single port to any destination in 10.0.0.0/24*Note: Copied from https://kubernetes.io/docs/concepts/services-networking/network-policies/
- 1: The name of the NetworkPolicy
- 2: The namespace the NetworkPolicy is assigned to
- 3: The Pods that are in scope for this NetworkPolicy. {} implies all Pods will be in scope
- 4: The direction of the traffic we want to control (in this case, its all ingress to all Pods)
kubectl create ns no-ingress-allowed.
Alternatively, you could either remove line 2 and this will result in the NetworkPolicy being applied in the default namespace.
Step 2: Implement the new NetworkPolicy.
$ kubectl create -f deny-all-ingress.yaml
Step 3: Create 2 Pods for testing the NetworkPolicy.
Using
$ kubectl apply -f deny-all-ingress-pods.yaml
set up the 2 Pods.
Step 4: Test Inter Pod communication.
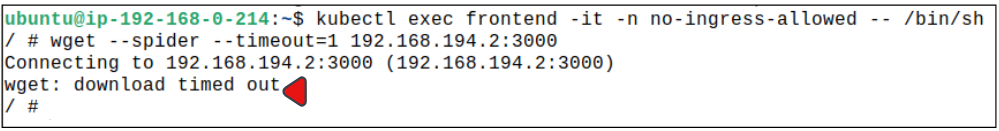
Since the NetworkPolicy wants no ingress for any Pod (regardless of who is trying to ingress) in the no-ingress-allowed namespace, we should not be able to get to the backend Pod from the frontend Pod (and vice versa).
For our test, we will exec into the frontend Pod and once there, attempt a wget call to the backend Pod.
I write to remember and if in the process, I can help someone learn about Containers, Orchestration (Docker Compose, Kubernetes), GitOps, DevSecOps, VR/AR, Architecture, and Data Management, that is just icing on the cake.